LOTTE Shopping has established policies and guidelines for information protection,
adopted top-level information protection policies as internal regulations to ensure that employees
and executives comply with laws and systems related to information security
and personal information protection, and continuously maintained the ISMS.
ISMS
LOTTE Shopping acquires and maintains Information Security Management System (ISMS) certification under the Information Security laws
and runs certification reviews for certification renewal and maintenance.
| Classification | Valid period | Certification scope |
|---|---|---|
| Department Store | From October 2021 to October 2024 |
Operation of online service for LOTTE Department Store (website, Culture Center, wedding) |
| Mart | From November 2020 to November 2023 |
Operation of online service for LOTTE Mart Culture Center |
| Super | From February 2022 to February 2025 |
Operation of online service for LOTTE Super (Main website, Shared Growth website, Business Information System, Partners’ portal) |
| E-Commerce | From February 2022 to February 2025 |
Operation of online service for online shopping mall (LOTTE ON, CONRANSHOP, MUJI, mobile gift certificate, e-coupon) |
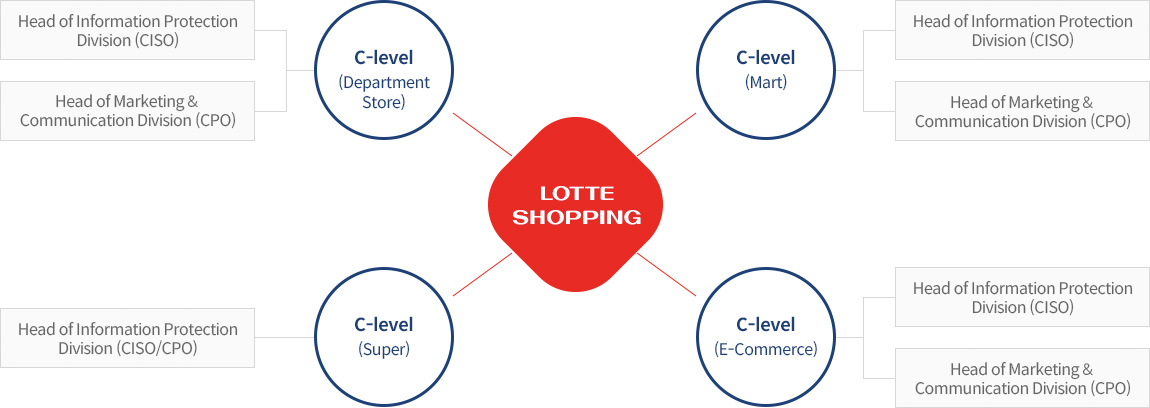
Information Security Organization
LOTTE Shopping has appointed the Chief Information Security Officer (CISO) to operate the Information Security Management System under domestic information protection laws and formed a dedicated information security organization to manage LOTTE Shopping’s information security comprehensively.
Information Protection Policy
| LOTTE Shopping Information Protection Policy (Regulation) | |||
|---|---|---|---|
| LOTTE Shopping Information Protection Guidelines (9) | Personal Information Protection Guidelines for each Business Division (1) | ||
| Management Areas (5) | Physical Area (1) | Technological Area (3) | Personal Information Area (1) |
| Operation of Information Protection Organization, Management of Information Asset, Personnel Security, Employee Management, Outsourcing Management | Physical Security | IT Security, Operation of Cloud, Management of Electronic Finance Security | Personal Information Protection Guidelines (Internal Management Plan) |
Procedure and Method